AutoDLCon: An Approach for Controlling the Automated Tuning for Deep Learning Networks
Neural networks have become the main building block on revolutionizing the field of artificial intelligence aided applications. With the wide availability of data and the increasing capacity of computing resources, they triggered a new era of state-of-the-art results in diverse directions. However, building neural network models is domain-specific, and figuring out the best architecture and hyper-parameters in each problem is still an art. In practice, it is a highly iterative process that is very time-consuming, requires substantial computing resources, and needs deep knowledge and solid
Transverse momentum spectra of strange hadrons within extensive and nonextensive statistics
Using generic (non)extensive statistics, in which the underlying system likely autonomously manifests its extensive and nonextensive statistical nature, we extract various fit parameters from the CMS experiment and compare these to the corresponding results obtained from Tsallis and Boltzmann statistics. The present study is designed to indicate the possible variations between the three types of statistical approaches and characterizes their dependence on collision energy, multiplicity, and size of the system of interest. We analyze the transverse momentum spectra pT of the strange hadrons Ks
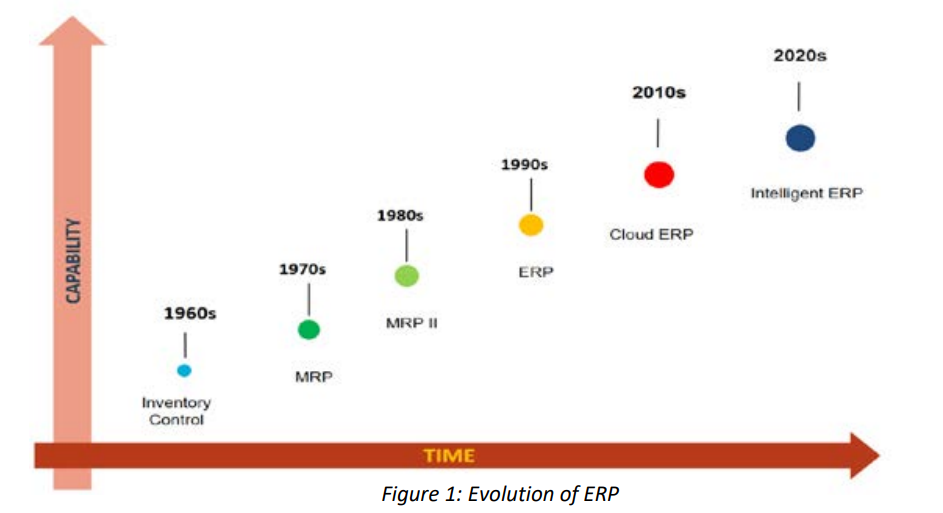
Guidelines for selecting emerging technology features for cloud erp
Emerging technologies such as Artificial Intelligence (AI), Blockchain and Internet of Things (IoT) permeate every aspect of work and life. For example, in the supply chain management: IoT-networked sensors can provide real-time insight into the provenance of goods and materials, supplier performance, available capacity, predictive demand and other key data. In turn, this data can feed autonomous and intelligent processes that “learn” how to respond to changing circumstances. Classical ERP systems do not support this distributed innovation. Emerging Technologies in Cloud ERP are what brings
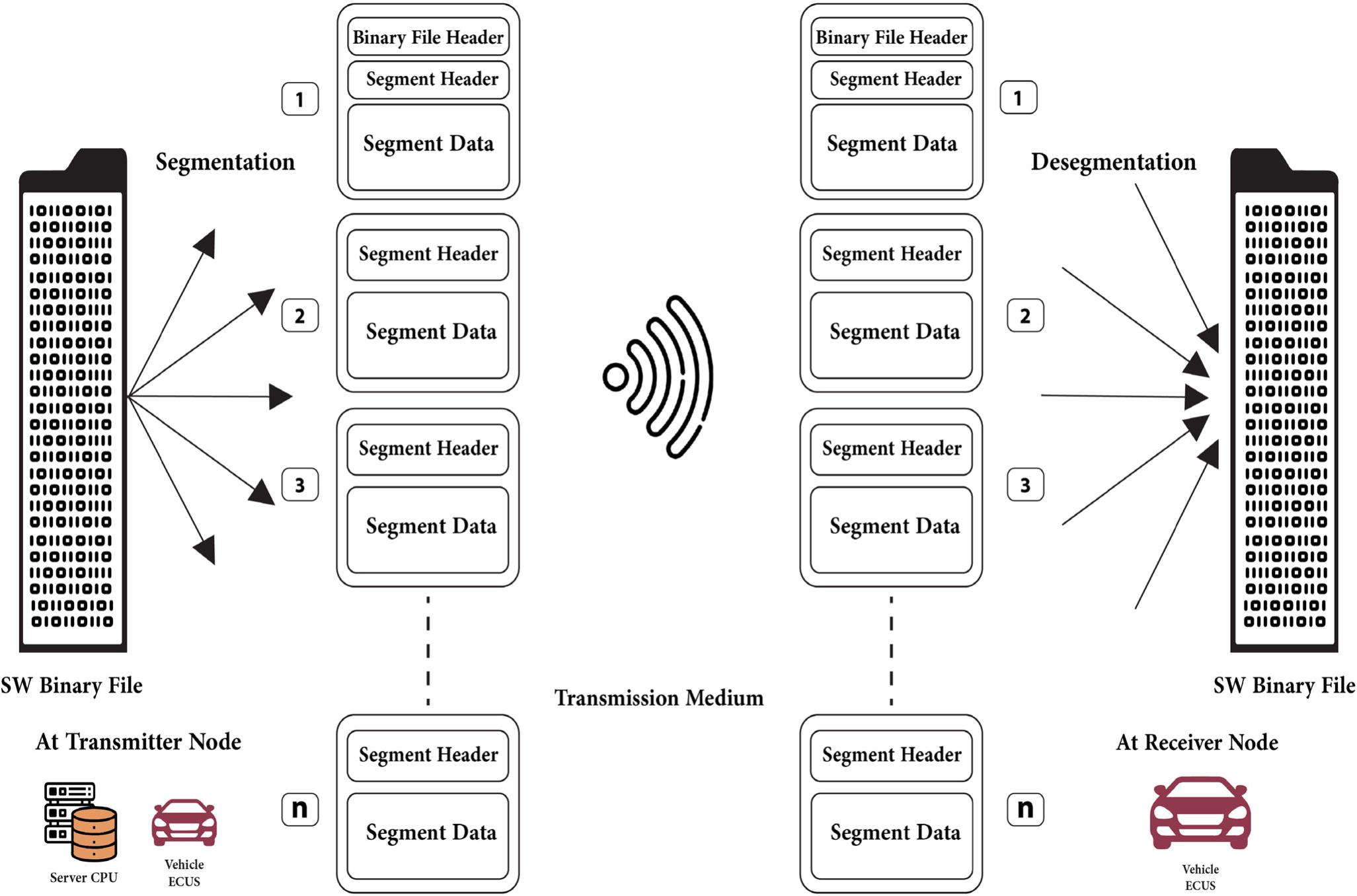
Segmented OTA Platform Over ICN Vehicular Networks
The Internet Protocol (IP) architecture could not fully satisfy the Vehicular Ad-hoc Networks (VANETs) needed efficiency, due to their dynamic topology and high mobility. This paper presents a technique that updates the software of Electronic Control Units (ECUs) in vehicles using segmented Over The Air (OTA) platform over Information-Centric Network (ICN) architecture. In VANET, the amount of time for active vehicles’ connectivity varies due to the vehicular network’s dynamic topologies. The importance of Flashing Over The Air (FOTA) has been illustrated as well as the impact of applying the
Cloud computing privacy issues, challenges and solutions
There are many cloud computing initiatives that represent a lot of benefit to enterprise customers. However, there are a lot of challenges and concerns regarding the security and the privacy of the customer data that is hosted on the cloud. We explore in this paper the various aspects of cloud computing regarding data life cycle and its security and privacy challenges along with the devised methodology to address those challenges. We mention some of the regulations and law requirements in place to ensure cloud customer data privacy. © 2017 IEEE.
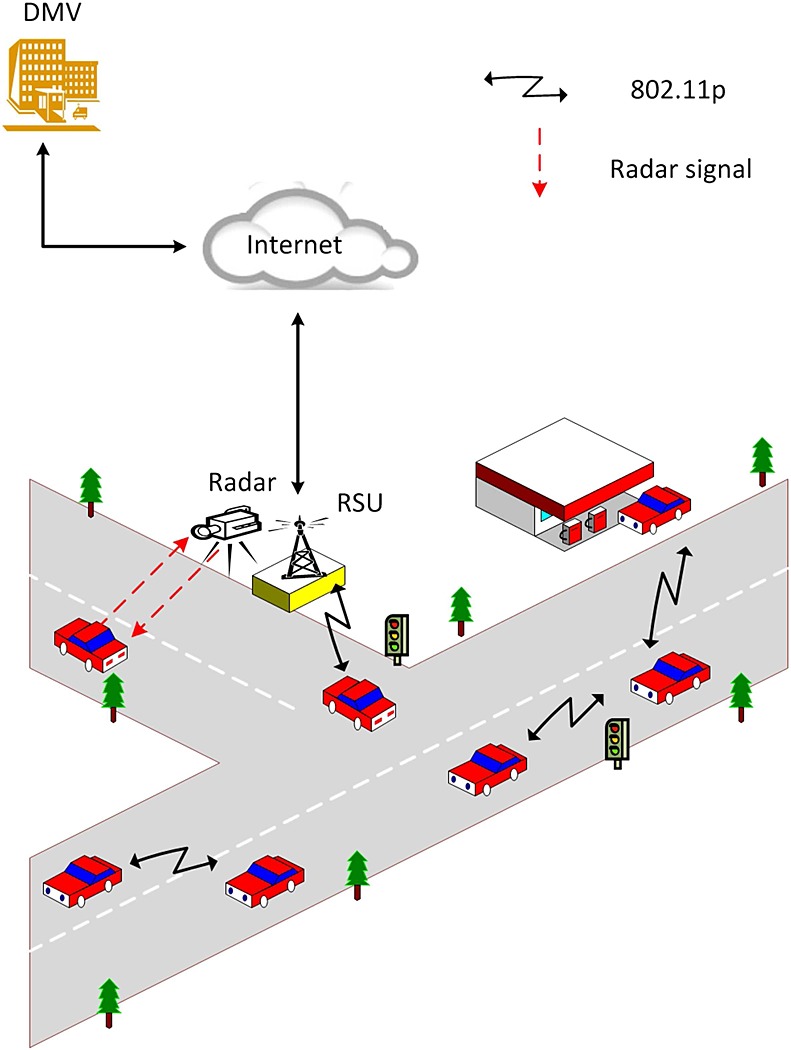
A secure and privacy-preserving event reporting scheme for vehicular Ad Hoc networks
In vehicular ad hoc networks, vehicles should report events to warn the drivers of unexpected hazards on the roads. While these reports can contribute to safer driving, vehicular ad hoc networks suffer from various security threats; a major one is Sybil attacks. In these attacks, an individual attacker can pretend as several vehicles that report a false event. In this paper, we propose a secure event-reporting scheme that is resilient to Sybil attacks and preserves the privacy of drivers. Instead of using asymmetric key cryptography, we use symmetric key cryptography to decrease the
Evaluating the Modsecurity Web Application Firewall against SQL Injection Attacks
SQL injection attacks target databases of web servers. The ability to modify, update, retrieve and delete database contents imposes a high risk on any website in different sectors. In this paper, we investigate the efforts done in the literature to detect and prevent the SQL injection attacks. We also assess the efficiency of the Modsecurity web application firewall in preventing SQL injection attacks. © 2020 IEEE.
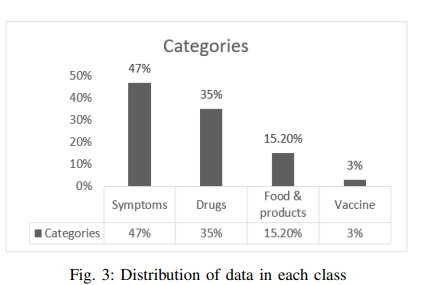
Intelligent Arabic-Based Healthcare Assistant
Text classification has been one of the most common natural language processing (NLP) objectives in recent years. Compared to other languages, this mission with Arabic is relatively restricted and in its early stages, and this combination in the medical application area is rare. This paper builds an Arabic health care assistant, specifically a pediatrician that supports Arabic dialects, especially Egyptian accents. The proposed application is a chatbot based on Artificial Intelligence (AI) models after experimenting with Two Bidirectional Encoder Representations from Transformers (BERT) models
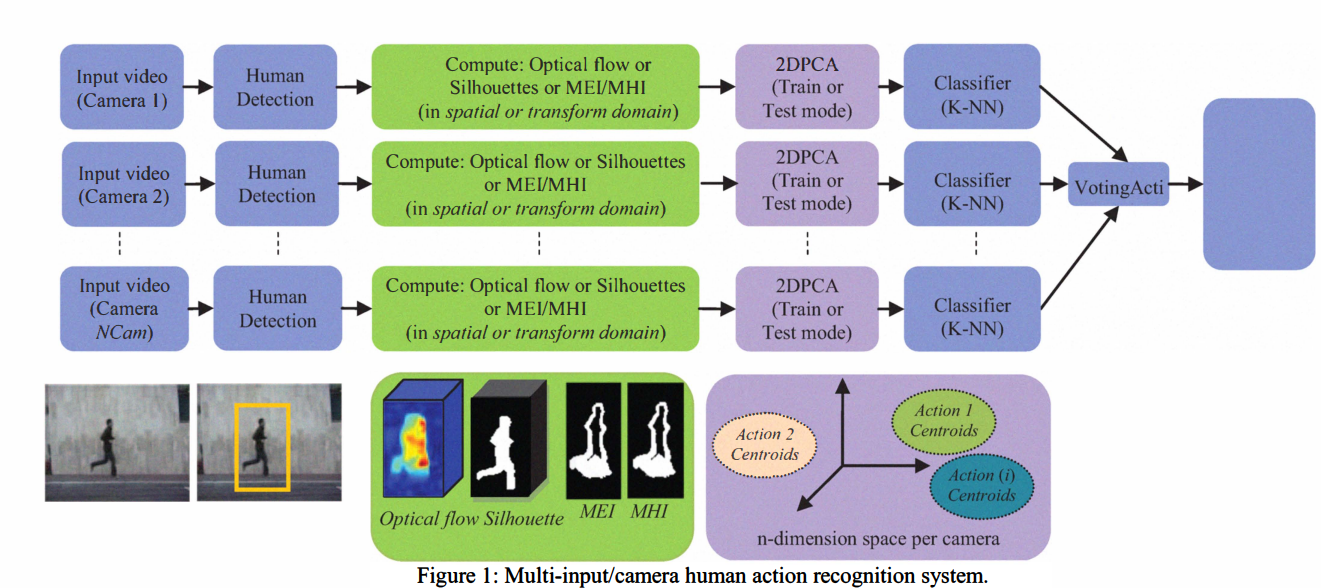
Highly efficient human action recognition using compact 2DPCA-based descriptors in the spatial and transform domains
Human action recognition is considered as a challenging problem in the field of computer vision. Most of the reported algorithms are computationally expensive. In this paper, a novel system for human action recognition based on Two-Dimensional Principal Component Analysis (2DPCA) is presented. This method works directly on the optical flow and / or silhouette extracted from the input video in both the spatial domain and the transform domain. The algorithm reduces the computational complexity and storage requirements, while achieving high recognition accuracy, compared with the most recent
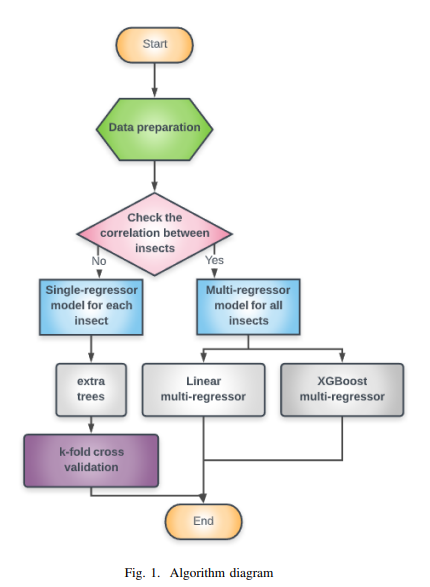
Guava Trees Disease Monitoring Using the Integration of Machine Learning and Predictive Analytics
The increase in population, food demand, and the pollution levels of the environment are considered major problems of this era. For these reasons, the traditional ways of farming are no longer suitable for early and accurate detection of biotic stress. Recently, precision agriculture has been extensively used as a potential solution for the aforementioned problems using high resolution optical sensors and data analysis methods that are able to cope with the resolution, size and complexity of the signals from these sensors. In this paper, several methods of machine learning have been utilized
Pagination
- Previous page ‹‹
- Page 14
- Next page ››
