Assessment of cardiac mass from tagged magnetic resonance images
Purpose: Tagged and cine magnetic resonance imaging (tMRI and cMRI) techniques are used for evaluating regional and global heart function, respectively. Measuring global function parameters directly from tMRI is challenging due to the obstruction of the anatomical structure by the tagging pattern. The purpose of this study was to develop a method for processing the tMRI images to improve the myocardium-blood contrast in order to estimate global function parameters from the processed images. Materials and methods: The developed method consists of two stages: (1) removing the tagging pattern
Real-Time Dorsal Hand Recognition Based on Smartphone
The integration of biometric recognition with smartphones is necessary to increase security, especially in financial transactions such as online payments. Vein recognition of the dorsal hand is superior to other methods such as palm, finger, and wrist, as it has a wide area to be captured and does not have any wrinkles. Most current systems that depend on dorsal hand vein recognition do not work in real-time and have poor results. In this paper, a dorsal hand recognition system working in real-time is proposed to achieve good results with a high frame rate. A contactless device consists of a
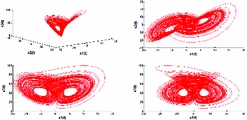
Control of new type of fractional chaos synchronization
Based on stability theory of linear fractional order systems and stability theory of linear integer order systems, the problem of coexistence of various types of synchronization between different dimensional fractional chaotic systems is investigated in this paper. Numerical and simulation results have clearly shown the effectiveness of the novel approach developed herein. © 2018, Springer International Publishing AG.
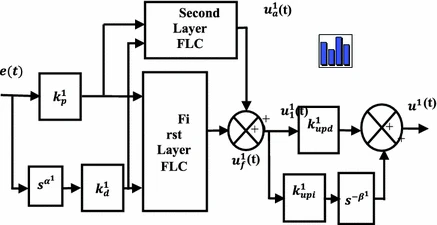
Control of a two link planar electrically-driven rigid robotic manipulator using fractional order SOFC
An intelligent adaptive fuzzy logic control technique, Fractional Order Self Organizing Fuzzy Controller (FOSOFC) is presented and applied to control a two link planar electrically-driven rigid robotic (EDRR) manipulator system. As EDRR is a multi-input multi-output complex nonlinear system, an intelligent adaptive controller, FOSOFC is considered to control it perfectly. To show the efficacy of the FOSOFC controller, the obtained performance is compared with fractional order fuzzy proportional integral and derivative (FOFPID) controller for study in servo as well as the regulatory problems
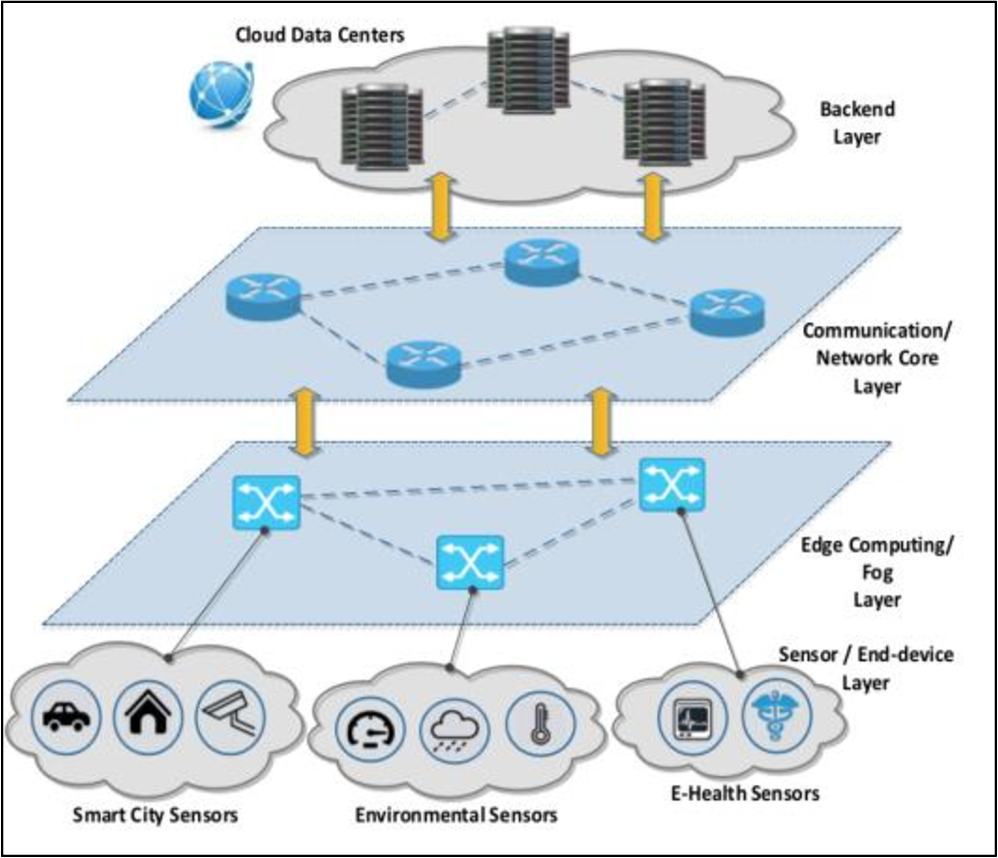
IoT Modes of Operations with Different Security Key Management Techniques: A Survey
The internet of things (IoT) has provided a promising opportunity to build powerful systems and applications. Security is the main concern in IoT applications due to the privacy of exchanged data using limited resources of IoT devices (sensors/actuators). In this paper, we present a classification of IoT modes of operation based on the distribution of IoT devices, connectivity to the internet, and the typical field of application. It has been found that the majority of IoT services can be classified into one of four IoT modes: Gateway, device to device, collaborative, and centralized. The
Towards mature temporal accuracy assessment of processors models and simulators for real-time systems development
Modeling and simulation are becoming extensively used in embedded and Real-Time Systems (RTSs) development throughout the development life-cycle, from the system-level design space exploration to the fine grained time analysis and evaluation of the system and even its components performance. At the core of these systems lies the processor which has been also the center of attention for most of the modeling and simulation efforts related to RTS simulation. Although the temporal accuracy of such models and simulators is of critical importance for Real-Time (RT) applications, it is not yet mature
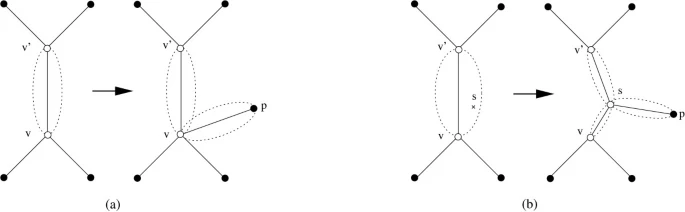
A fast algorithm for the multiple genome rearrangement problem with weighted reversals and transpositions
Background: Due to recent progress in genome sequencing, more and more data for phylogenetic reconstruction based on rearrangement distances between genomes become available. However, this phylogenetic reconstruction is a very challenging task. For the most simple distance measures (the breakpoint distance and the reversal distance), the problem is NP-hard even if one considers only three genomes. Results: In this paper, we present a new heuristic algorithm that directly constructs a phylogenetic tree w.r.t. the weighted reversal and transposition distance. Experimental results on previously
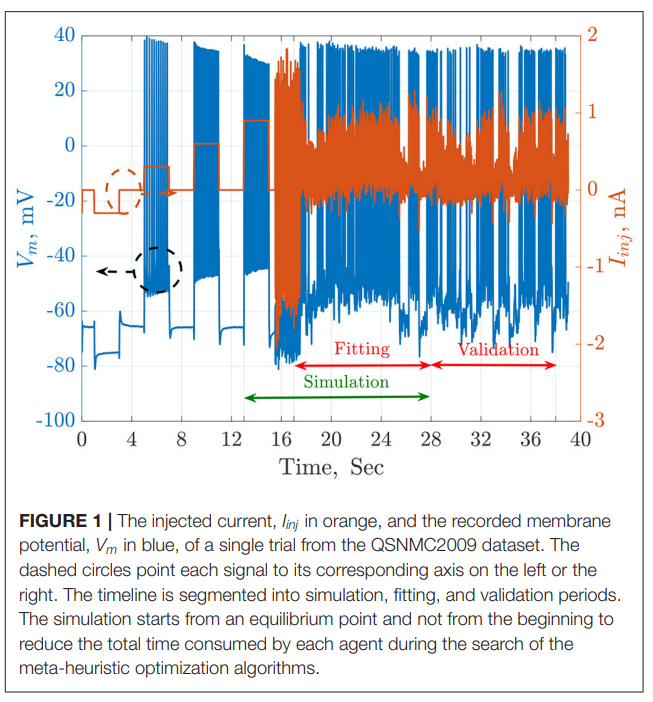
Parameter Estimation of Two Spiking Neuron Models With Meta-Heuristic Optimization Algorithms
The automatic fitting of spiking neuron models to experimental data is a challenging problem. The integrate and fire model and Hodgkin–Huxley (HH) models represent the two complexity extremes of spiking neural models. Between these two extremes lies two and three differential-equation-based models. In this work, we investigate the problem of parameter estimation of two simple neuron models with a sharp reset in order to fit the spike timing of electro-physiological recordings based on two problem formulations. Five optimization algorithms are investigated; three of them have not been used to
Constructing suffix array during decompression
The suffix array is an indexing data structure used in a wide range of applications in Bioinformatics. Biological DNA sequences are available to download from public servers in the form of compressed files, where the popular lossless compression program gzip [1] is employed. The straightforward method to construct the suffix array for this data involves decompressing the sequence file, storing it on disk, and then calling a suffix array construction program to build the suffix array. This scenario, albeit feasible, requires disk access and throws away valuable information in the compressed
Recognizing Clothing Patterns and Colors for BVI People Using Different Techniques
For blind and visually impaired (BVI) people, it is an arduous task to recognize clothing patterns and colors. It is especially complex to recognize them automatically. This is a highly researched area in image processing. This paper provides BVI with the ability to detect patterns and colors without depending on personal assistance, leading to increasing their confidence. The user first captures an image; then, our system detects colors and patterns. The color model used here is the hue saturation value (HSV). The main colors detected by our system are magenta, cyan, blue, green, red and
Pagination
- Previous page ‹‹
- Page 13
- Next page ››
