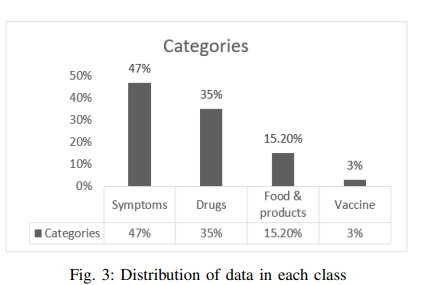
Intelligent Arabic-Based Healthcare Assistant
Text classification has been one of the most common natural language processing (NLP) objectives in recent years. Compared to other languages, this mission with Arabic is relatively restricted and in its early stages, and this combination in the medical application area is rare. This paper builds an Arabic health care assistant, specifically a pediatrician that supports Arabic dialects, especially Egyptian accents. The proposed application is a chatbot based on Artificial Intelligence (AI) models after experimenting with Two Bidirectional Encoder Representations from Transformers (BERT) models
Evaluating the Modsecurity Web Application Firewall against SQL Injection Attacks
SQL injection attacks target databases of web servers. The ability to modify, update, retrieve and delete database contents imposes a high risk on any website in different sectors. In this paper, we investigate the efforts done in the literature to detect and prevent the SQL injection attacks. We also assess the efficiency of the Modsecurity web application firewall in preventing SQL injection attacks. © 2020 IEEE.
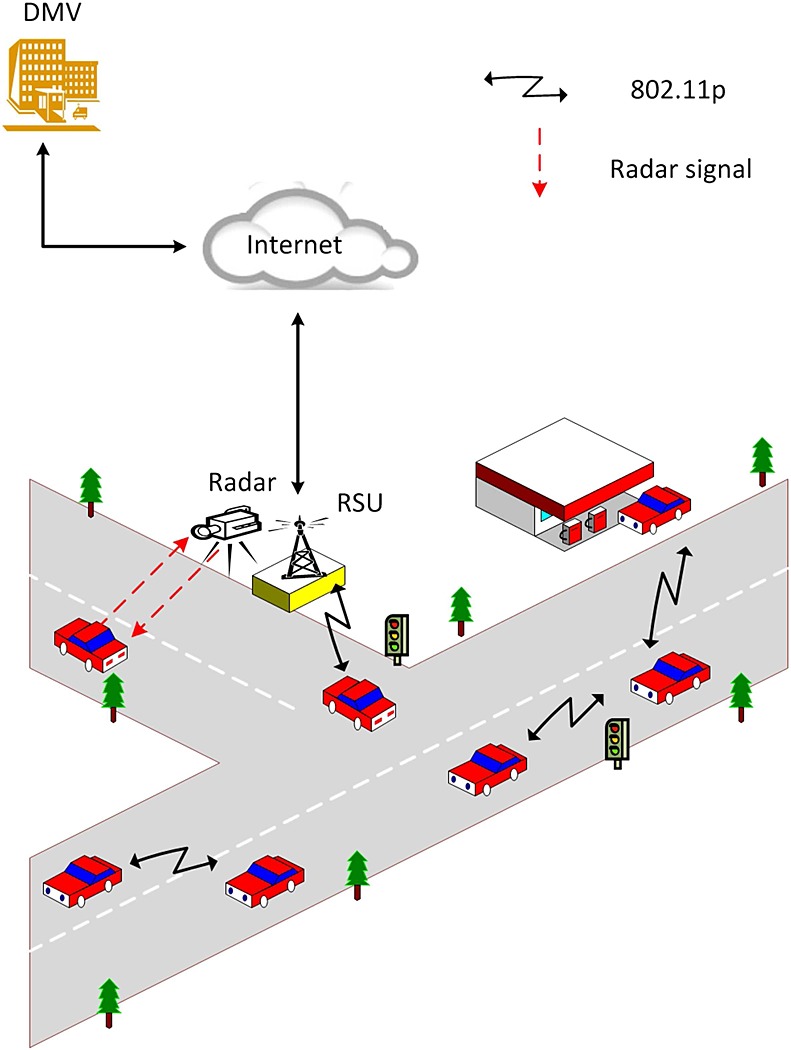
A secure and privacy-preserving event reporting scheme for vehicular Ad Hoc networks
In vehicular ad hoc networks, vehicles should report events to warn the drivers of unexpected hazards on the roads. While these reports can contribute to safer driving, vehicular ad hoc networks suffer from various security threats; a major one is Sybil attacks. In these attacks, an individual attacker can pretend as several vehicles that report a false event. In this paper, we propose a secure event-reporting scheme that is resilient to Sybil attacks and preserves the privacy of drivers. Instead of using asymmetric key cryptography, we use symmetric key cryptography to decrease the
Cloud computing privacy issues, challenges and solutions
There are many cloud computing initiatives that represent a lot of benefit to enterprise customers. However, there are a lot of challenges and concerns regarding the security and the privacy of the customer data that is hosted on the cloud. We explore in this paper the various aspects of cloud computing regarding data life cycle and its security and privacy challenges along with the devised methodology to address those challenges. We mention some of the regulations and law requirements in place to ensure cloud customer data privacy. © 2017 IEEE.
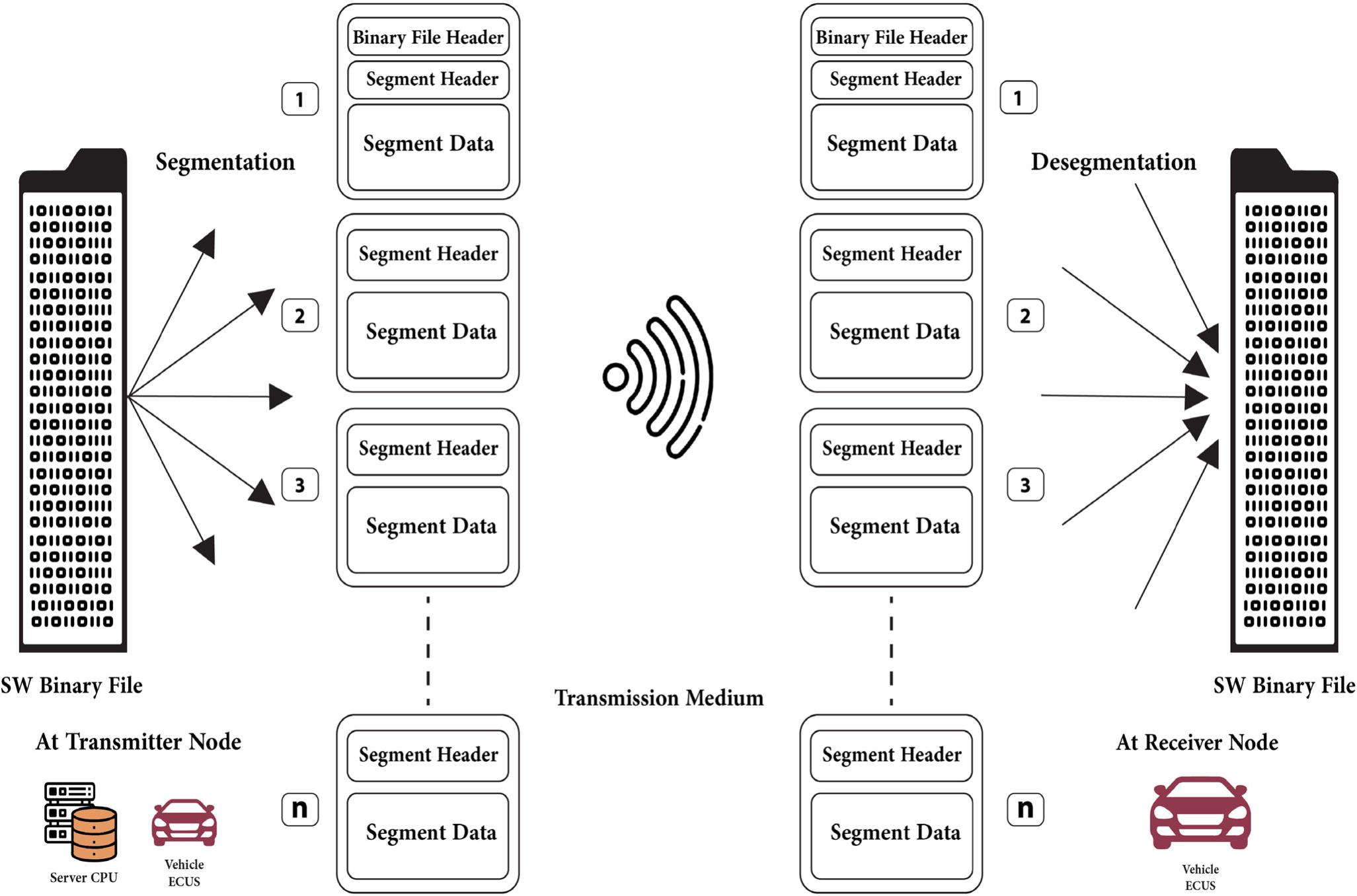
Segmented OTA Platform Over ICN Vehicular Networks
The Internet Protocol (IP) architecture could not fully satisfy the Vehicular Ad-hoc Networks (VANETs) needed efficiency, due to their dynamic topology and high mobility. This paper presents a technique that updates the software of Electronic Control Units (ECUs) in vehicles using segmented Over The Air (OTA) platform over Information-Centric Network (ICN) architecture. In VANET, the amount of time for active vehicles’ connectivity varies due to the vehicular network’s dynamic topologies. The importance of Flashing Over The Air (FOTA) has been illustrated as well as the impact of applying the
Motion history of skeletal volumes and temporal change in bounding volume fusion for human action recognition
Human action recognition is an important area of research in computer vision. Its applications include surveillance systems, patient monitoring, human-computer interaction, just to name a few. Numerous techniques have been developed to solve this problem in 2D and 3D spaces. However 3D imaging gained a lot of interest nowadays. In this paper we propose a novel view-independent action recognition algorithm based on fusion between a global feature and a graph based feature. We used the motion history of skeleton volumes; we compute a skeleton for each volume and a motion history for each action
Face and gesture recognition for human computer interaction employing 2DHoG
Face and hand gesture recognition is one of the most challenging topics in computer vision. In this paper, a novel algorithm presenting a new 2D representation of histogram of oriented gradients is proposed, where each bin represents a range of angles dealt with in a separate layer employing 2DPCA. This method maintains the spatial relation between pixels which enhance the recognition accuracy. In addition it can be applied on either face or hand gesture images. Experimental results confirm excellent properties of the proposed algorithm and promotes it for real time applications © 2013 IEEE.
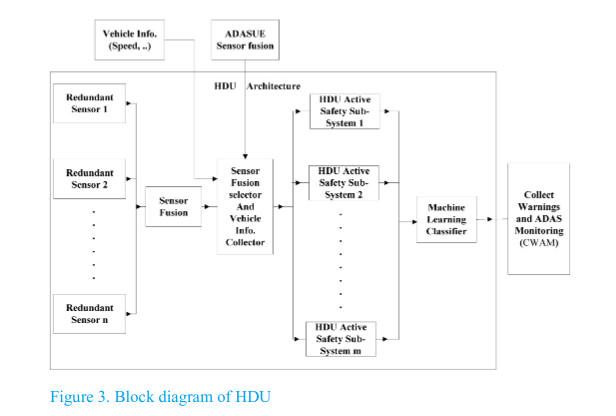
On Board Evaluation System for Advanced Driver Assistance Systems
The evaluation of Advanced Driver Assistance Systems (ADAS including driver assistance and active safety) has increasing interest from authorities, industry and academia. AsPeCSS active safety project concludes that good results in a laboratory test for active safety system design does not necessarily equate to an effective system in real traffic conditions. Moreover, many ADAS assessment projects and standards require physical testing on test tracks (dummy vehicles, pedestrian mannequins.), which are expensive and limit testing capabilities. This research presents a conceptual framework for
DiSGD: A distributed shared-nothing matrix factorization for large scale online recommender systems
With the web-scale data volumes and high velocity of generation rates, it has become crucial that the training process for recommender systems be a continuous process which is performed on live data, i.e., on data streams. In practice, such systems have to address three main requirements including the ability to adapt their trained model with each incoming data element, the ability to handle concept drifts and the ability to scale with the volume of the data. In principle, matrix factorization is one of the popular approaches to train a recommender model. Stochastic Gradient Descent (SGD) has
Simultaneous human detection and action recognition employing 2DPCA-HOG
In this paper a novel algorithm for Human detection and action recognition in videos is presented. The algorithm is based on Two-Dimensional Principal Components Analysis (2DPCA) applied to Histogram of Oriented Gradients (HOG). Due to simultaneous Human detection and action recognition employing the same algorithm, the computational complexity is reduced to a great deal. Experimental results applied to public datasets confirm these excellent properties compared to most recent methods. © 2011 IEEE.
Pagination
- Previous page ‹‹
- Page 15
- Next page ››
