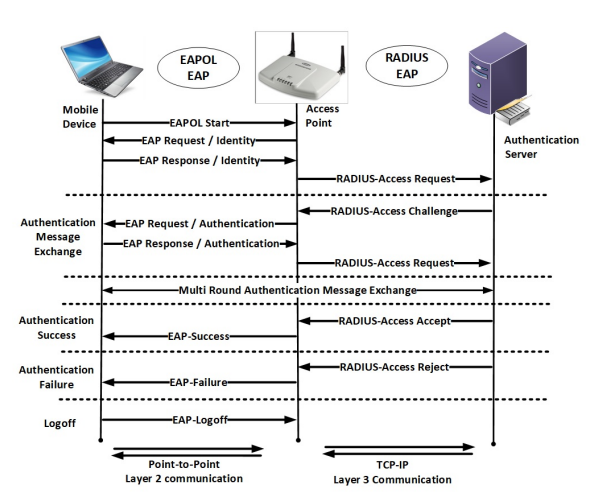
A study in WPA2 enterprise recent attacks
Organizations and network developers continuously exert much money and efforts to secure wireless transmission. WPA2 framework is widely deployed for Wi-Fi communications since it is efficient and secure against several wireless attacks. However, WPA2 security has been lately threatened by advanced developed versions of wireless attacks. The increase of computer processing power, continuous efforts by penetration testers, network evaluators and researchers led to the emerging of new advanced attacking techniques that may exploit WPA2 wireless systems detected vulnerabilities. In this paper, we
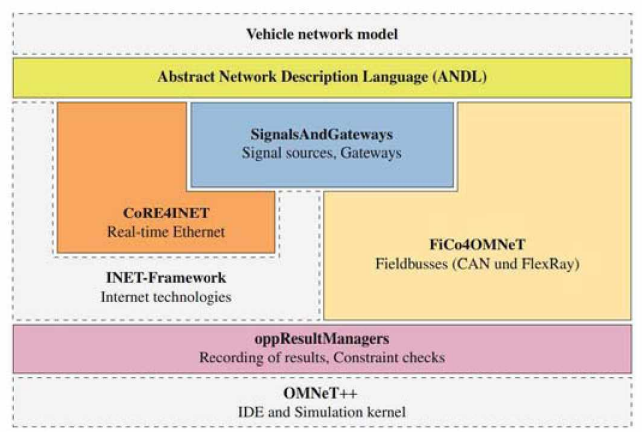
AVB/TSN Protocols in Automotive Networking
In the last decade, Ethernet networks that require real time constraints are massively increased. Switched Ethernet is reshaping in-vehicle communications. To meet real-time requirements for diverse data types in automotive communications, Quality-of-Service protocols that go beyond the mere use of priorities are required. In Vehicle networks requirements are evolving and need better Quality-of-Service (QoS) options. This applies also for industrial networks implementation. Time Sensitive Networking (TSN) IEEE 802.1 Task working group are providing wide variety of Standard. This standard
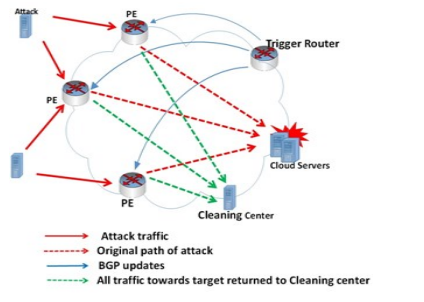
Detection and Countermeasures of DDoS Attacks in Cloud Computing
Greater portions of the world are moving to cloud computing because of its advantages However, due to its distributed nature, it can be easily exploited by Distributed Denial of Service (DDoS) attacks. In distributed DDoS attacks, legitimate users are prevented from using cloud resources. In this paper, the various DDoS detection and defenses mechanisms cloud computing are reviewed. We propose a new technique based on Remote Triggered Black Hole (RTBH) to prevent DDoS attacks before it target to cloud resources. © 2018 IEEE.
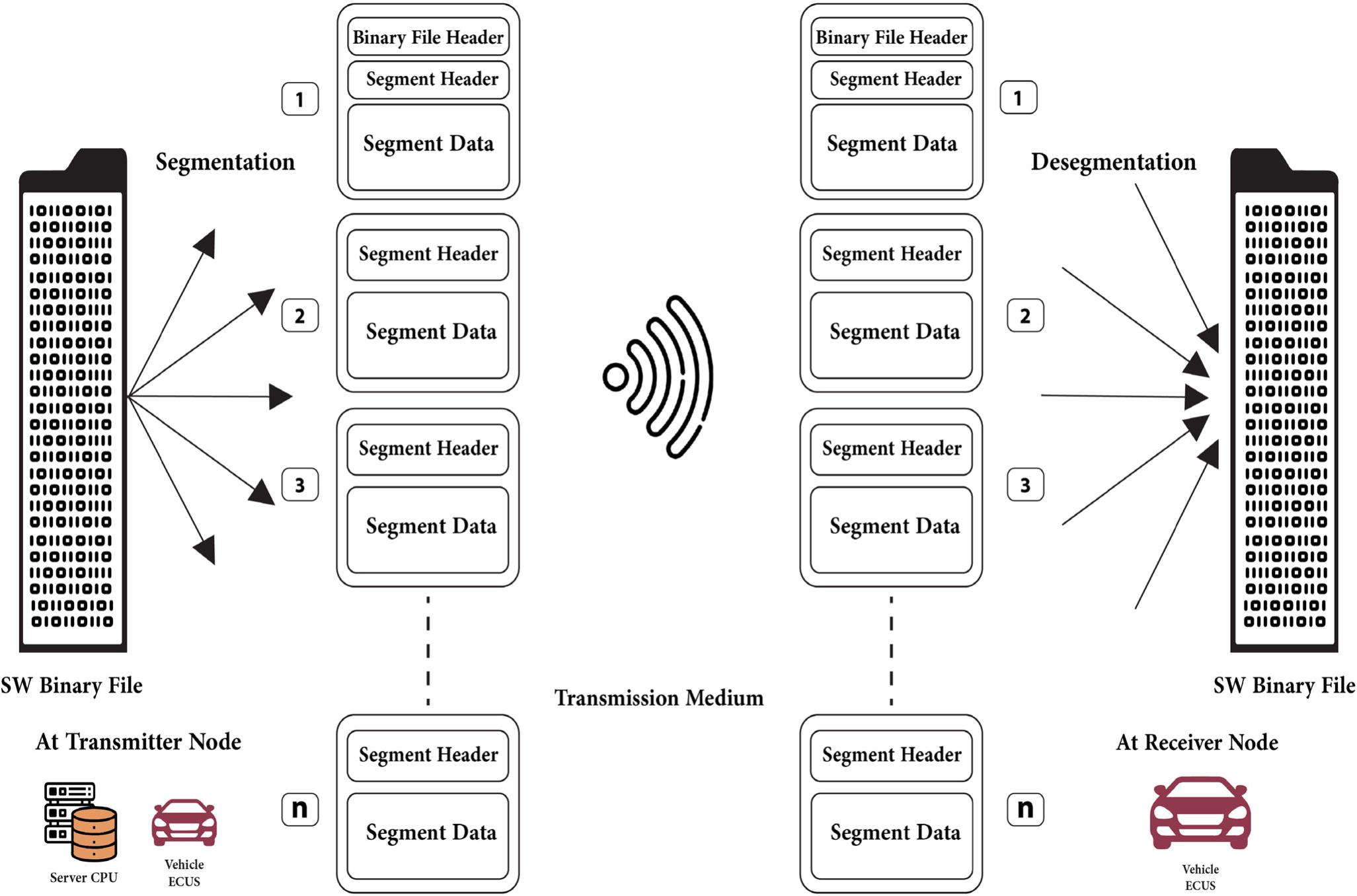
Segmented OTA Platform Over ICN Vehicular Networks
The Internet Protocol (IP) architecture could not fully satisfy the Vehicular Ad-hoc Networks (VANETs) needed efficiency, due to their dynamic topology and high mobility. This paper presents a technique that updates the software of Electronic Control Units (ECUs) in vehicles using segmented Over The Air (OTA) platform over Information-Centric Network (ICN) architecture. In VANET, the amount of time for active vehicles’ connectivity varies due to the vehicular network’s dynamic topologies. The importance of Flashing Over The Air (FOTA) has been illustrated as well as the impact of applying the
Cloud computing privacy issues, challenges and solutions
There are many cloud computing initiatives that represent a lot of benefit to enterprise customers. However, there are a lot of challenges and concerns regarding the security and the privacy of the customer data that is hosted on the cloud. We explore in this paper the various aspects of cloud computing regarding data life cycle and its security and privacy challenges along with the devised methodology to address those challenges. We mention some of the regulations and law requirements in place to ensure cloud customer data privacy. © 2017 IEEE.
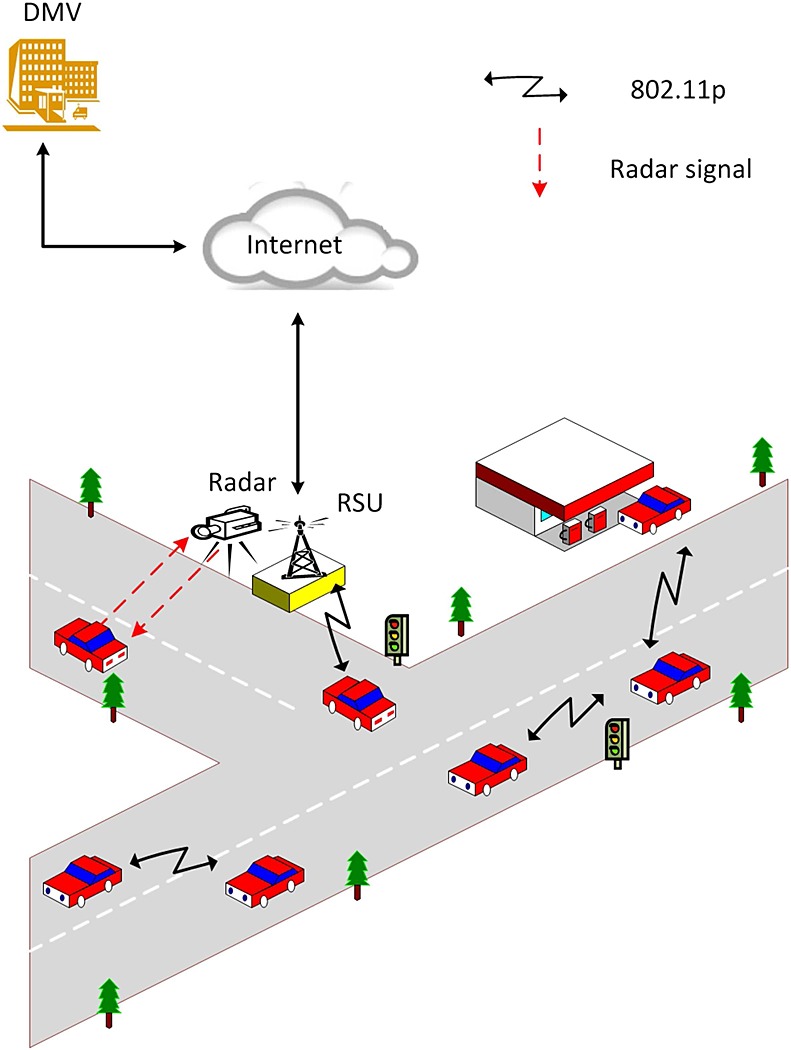
A secure and privacy-preserving event reporting scheme for vehicular Ad Hoc networks
In vehicular ad hoc networks, vehicles should report events to warn the drivers of unexpected hazards on the roads. While these reports can contribute to safer driving, vehicular ad hoc networks suffer from various security threats; a major one is Sybil attacks. In these attacks, an individual attacker can pretend as several vehicles that report a false event. In this paper, we propose a secure event-reporting scheme that is resilient to Sybil attacks and preserves the privacy of drivers. Instead of using asymmetric key cryptography, we use symmetric key cryptography to decrease the
Modeling the Production Planning and Control System using UML
Production planning and control systems are known for their complexity, especially for large scale production units. The Unified Modeling Language (UML) is known for its efficiency in modeling such complex systems for better visualization and as an initial step for software implementation. In this paper, UML is utilized to model production planning and control systems. The models developed include functional, and behavioral models represented through a use case diagram, an activity diagram, and a communication diagram. The proposed models serve as the first step towards implementing a software
Evaluating the Modsecurity Web Application Firewall against SQL Injection Attacks
SQL injection attacks target databases of web servers. The ability to modify, update, retrieve and delete database contents imposes a high risk on any website in different sectors. In this paper, we investigate the efforts done in the literature to detect and prevent the SQL injection attacks. We also assess the efficiency of the Modsecurity web application firewall in preventing SQL injection attacks. © 2020 IEEE.
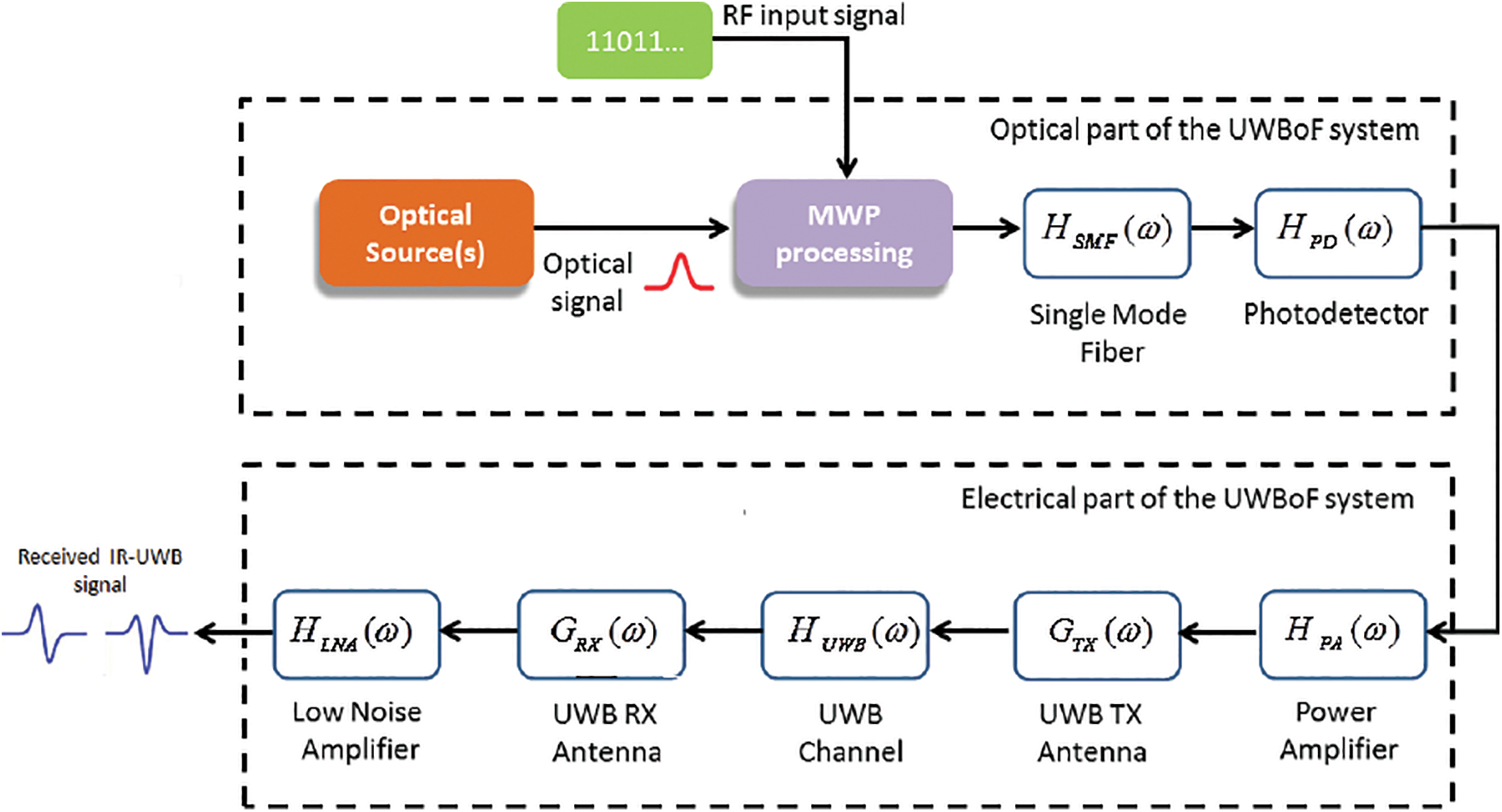
Radio optical network simulation tool (ronst)
This paper presents a radio optical network simulation tool (RONST) for modeling optical-wireless systems. For a typical optical and electrical chain environment, performance should be optimized concurrently before system implementation. As a result, simulating such systems turns out to be a multidisciplinary problem. The governing equations are incompatible with co-simulation in the traditional environments of existing software (SW) packages. The ultra-wideband (UWB) technology is an ideal candidate for providing high-speed short-range access for wireless services. The limited wireless reach
Coarse spectrum sensing for LTE systems
Spectrum sensing is one of the most challenging tasks required of a cognitive radio receiver. In this paper, we consider the first stage of spectrum sensing, where it is required to perform the sensing as fast as possible and with an acceptable performance under different channel conditions. The target signal to be sensed is a Long Term Evolution (LTE) signal. We first propose sensing the whole LTE signal bandwidth using the Fast Wavelet Transform (FWT) algorithm and then compare it to the Fast Fourier Transform (FFT)-based algorithm in terms of complexity and performance. A new algorithm is
Pagination
- Previous page ‹‹
- Page 56
- Next page ››
