Cluster Head election in Wireless Sensor Networks
Wireless Sensor Networks (WSNs) consist of a collection of cheap, easy to deploy Sensor nodes arranged together to fulfill a specific purpose (monitoring, tracking...etc.). A WSN network is composed of a Base Station (BS) and collection of sensors. There are a lot of approaches for the network construction. Amongst them is the hierarchical structure, where the network is divided into clusters and the node inside this cluster communicates with BS through a chosen leader called Cluster Head (CH). In this paper, we present cluster-Head election algorithms for WSNs. We will discuss the operations
Comparison study of digital forensics analysis techniques
Recently, digital forensics analysis got a great attention in IT security. This is especially after cyber incidents are getting new form of organized crime which introduced Advanced Persistent Threats (APT), and hacking Kill Chain definitions. The threat intense rises when it is affecting the healthcare organization where it will be life-threatening. Handling such incidents is a great challenge for handlers to uncover the attack steps. With various sources of evidential data that require analysis, one analysis technique can be more beneficial than another, comparing to the time and resources
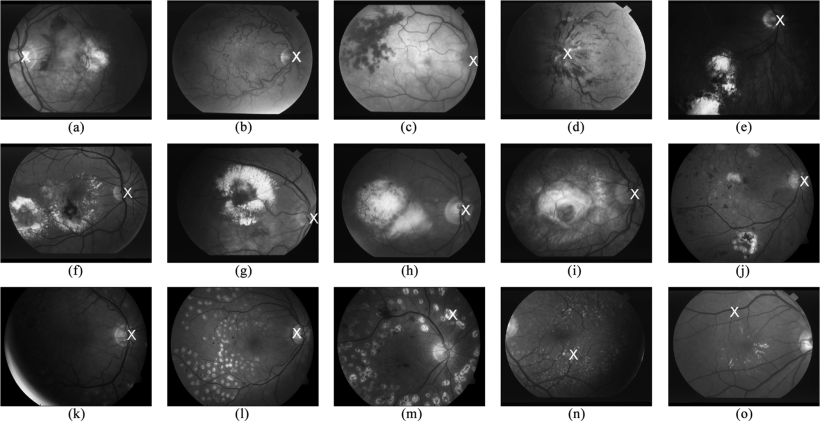
Fast localization of the optic disc using projection of image features
Optic Disc (OD) localization is an important pre-processing step that significantly simplifies subsequent segmentation of the OD and other retinal structures. Current OD localization techniques suffer from impractically-high computation times (few minutes per image). In this work, we present a fast technique that requires less than a second to localize the OD. The technique is based upon obtaining two projections of certain image features that encode the x- and y- coordinates of the OD. The resulting 1-D projections are then searched to determine the location of the OD. This avoids searching
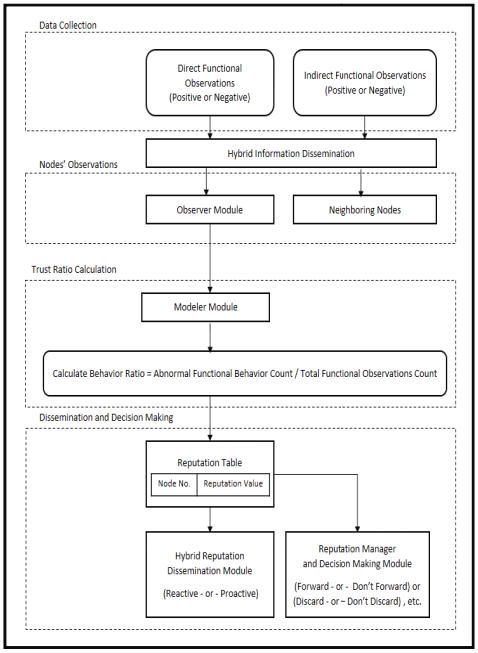
MDAC: A new reputation system for misbehavior detection and control in ad hoc networks
Reputation systems are an emerging area of research in ad-hoc networks. They have been introduced as a security solution for nodes' misbehaving problem. A reputation system should cope with any kind of misbehavior. It enables honest nodes to make fair decisions about their neighbors. This may encourage nodes to behave well and cooperate in order to avoid being penalized or isolated. In this paper, we propose a new reputation system for Misbehavior Detection And Control in ad hoc Networks (MDAC). It aims to overcome some of the unsolved issues of other reputation systems, and it is customizable
Sybil attack prevention through identity symmetric scheme in vehicular ad-hoc networks
Vehicular Ad-hoc Networks (VANETs) are a subset of Mobile Ad-hoc Networks (MANETs). They are deployed to introduce the ability of inter-communication among vehicles in order to guarantee safety and provide services for people while driving. VANETs are exposed to many types of attacks like denial of service, spoofing, ID disclosure and Sybil attacks. In this paper, a novel lightweight approach for preventing Sybil attack in VANETs is proposed. The presented protocol scheme uses symmetric key encryption and authentication between Road Side Units (RSUs) and vehicles on the road so that no
A detailed survey and future directions of unmanned aerial vehicles (Uavs) with potential applications
Recently, unmanned aerial vehicles (UAVs), also known as drones, have gained widespread interest in civilian and military applications, which has led to the development of novel UAVs that can perform various operations. UAVs are aircraft that can fly without the need of a human pilot onboard, meaning they can fly either autonomously or be remotely piloted. They can be equipped with multiple sensors, including cameras, inertial measurement units (IMUs), LiDAR, and GPS, to collect and transmit data in real time. Due to the demand for UAVs in various applications such as precision agriculture
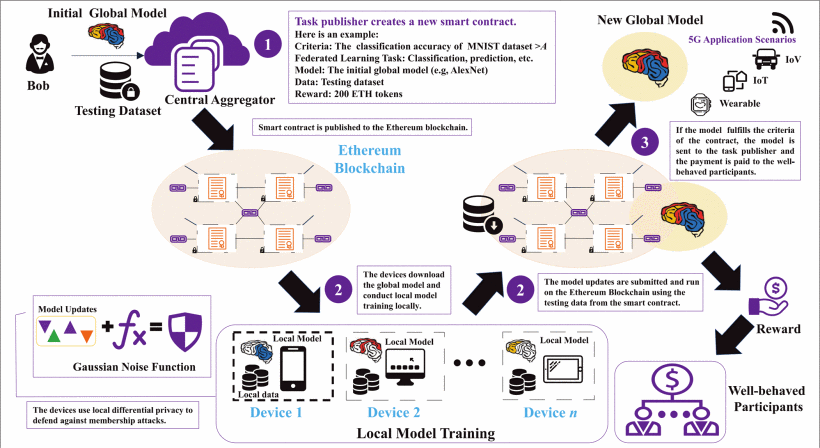
A Secure Federated Learning Framework for 5G Networks
Federated learning (FL) has recently been proposed as an emerging paradigm to build machine learning models using distributed training datasets that are locally stored and maintained on different devices in 5G networks while providing privacy preservation for participants. In FL, the central aggregator accumulates local updates uploaded by participants to update a global model. However, there are two critical security threats: poisoning and membership inference attacks. These attacks may be carried out by malicious or unreliable participants, resulting in the construction failure of global
Motion and depth augmented semantic segmentation for autonomous navigation
Motion and depth provide critical information in autonomous driving and they are commonly used for generic object detection. In this paper, we leverage them for improving semantic segmentation. Depth cues can be useful for detecting road as it lies below the horizon line. There is also a strong structural similarity for different instances of different objects including buildings and trees. Motion cues are useful as the scene is highly dynamic with moving objects including vehicles and pedestrians. This work utilizes geometric information modelled by depth maps and motion cues represented by
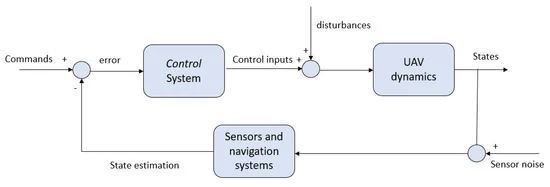
Remote Diagnosis, Maintenance and Prognosis for Advanced Driver Assistance Systems Using Machine Learning Algorithms
New challenges and complexities are continuously increasing in advanced driver assistance systems (ADAS) development (e.g. active safety, driver assistant and autonomous vehicle systems). Therefore, the health management of ADAS’ components needs special improvements. Since software contribution in ADAS’ development is increasing significantly, remote diagnosis and maintenance for ADAS become more important. Furthermore, it is highly recommended to predict the remaining useful life (RUL) for the prognosis of ADAS’ safety critical components; e.g. (Ultrasonic, Cameras, Radar, LIDAR). This paper
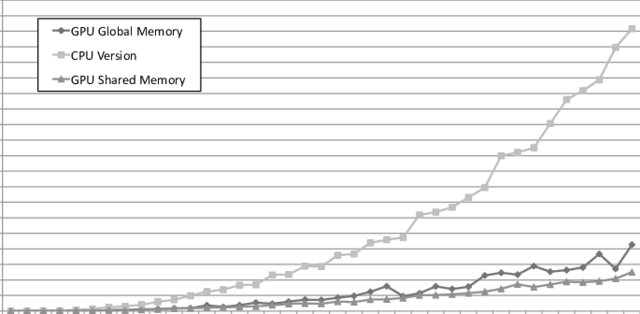
A GPU-enabled solver for time-constrained linear sum assignment problems
This paper deals with solving large instances of the Linear Sum Assignment Problems (LSAPs) under realtime constraints, using Graphical Processing Units (GPUs). The motivating scenario is an industrial application for P2P live streaming that is moderated by a central tracker that is periodically solving LSAP instances to optimize the connectivity of thousands of peers. However, our findings are generic enough to be applied in other contexts. Our main contribution is a parallel version of a heuristic algorithm called Deep Greedy Switching (DGS) on GPUs using the CUDA programming language. DGS
Pagination
- Previous page ‹‹
- Page 53
- Next page ››
