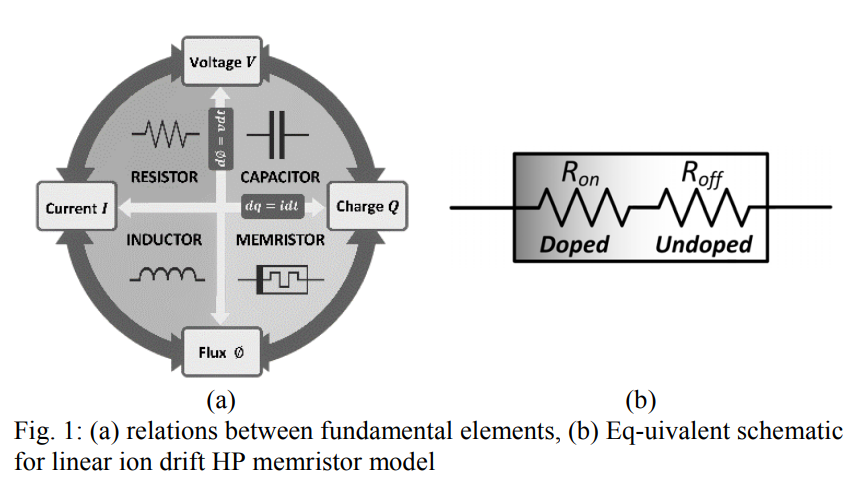
Reactance-less RM relaxation oscillator using exponential memristor model
Recently, the memristor based relaxation oscillators become an important topic in circuit theory where the reactive elements are replaced by memristor which occupies a very small area. In this paper, a design of memristor-based relaxation oscillator is introduced based on exponential memristor model. Unlike previously published oscillators which were built based on a simple memristor model, the exponential model is used, as a generalized model, to verify the concept of memristor based RM oscillator using a model that has electrical characteristic very close to the fabricated device. First, the

Chaos synchronisation of continuous systems via scalar signal
By analyzing the issue of chaos synchronization in the literature, it can be noticed the lack of a general approach, which would enable any type of synchronization to be achieved. Similarly, there is the lack of a unified method for synchronizing both continuous-time and discrete-time systems via a scalar signal. This paper and the companion one [1] aim to bridge these two gaps by presenting a novel general unified framework to synchronize chaotic systems via a scalar signal. The framework, based on the concept of observer, enables any type of synchronization defined to date to be achieved for
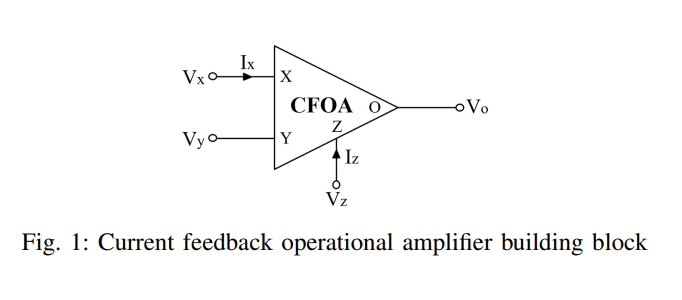
On the realization of Current-Mode Fractional-order Simulated Inductors
The objective of this work is to revisit the design criteria of current-mode simulated inductors in order to realize their fractional-order versions. Numerical simulations and SPICE circuits simulations are carried out on these generalized fractional-order simulated inductors. As well, fractional-order low pass filters based on the proposed circuits are realized and validated. © 2019 IEEE.
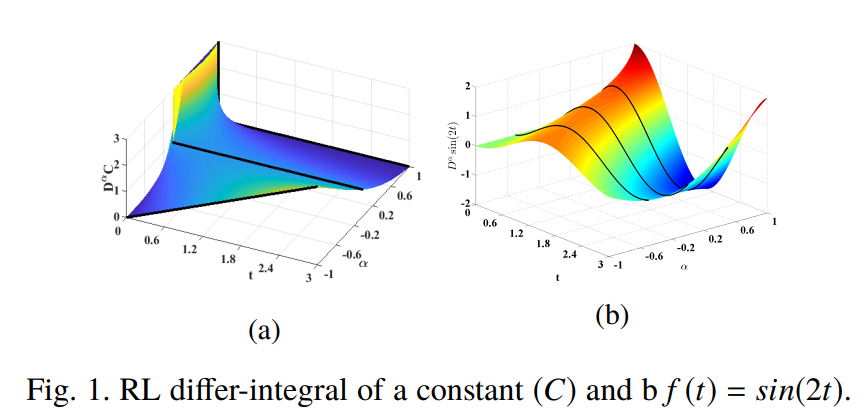
Fractional calculus definitions, approximations, and engineering applications
The basic idea behind fractional calculus is that it considers derivatives and integrals of non-integer orders giving extra degrees of freedom and tuning knobs for modeling complex and memory dependent systems with compact descriptions. This paper reviews fractional calculus history, theory, and its applications in electrical engineering. The basic definitions of fractional calculus are presented together with some examples. Integer order transfer function approximations and constant phase elements (CPEs) emulators are overviewed due to their importance in implementing fractional-order
Pagination
- Previous page ‹‹
- Page 19
- Next page ››

