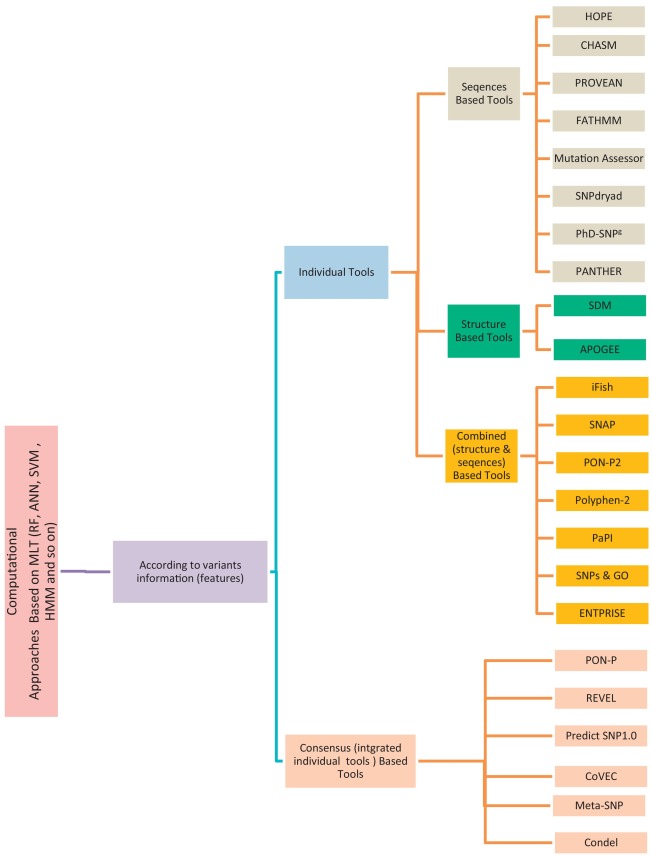
A review study: Computational techniques for expecting the impact of non-synonymous single nucleotide variants in human diseases
Non-Synonymous Single-Nucleotide Variants (nsSNVs) and mutations can create a diversity effect on proteins as changing genotype and phenotype, which interrupts its stability. The alterations in the protein stability may cause diseases like cancer. Discovering of nsSNVs and mutations can be a useful tool for diagnosing the disease at a beginning stage. Many studies introduced the various predicting singular and consensus tools that based on different Machine Learning Techniques (MLTs) using diverse datasets. Therefore, we introduce the current comprehensive review of the most popular and recent
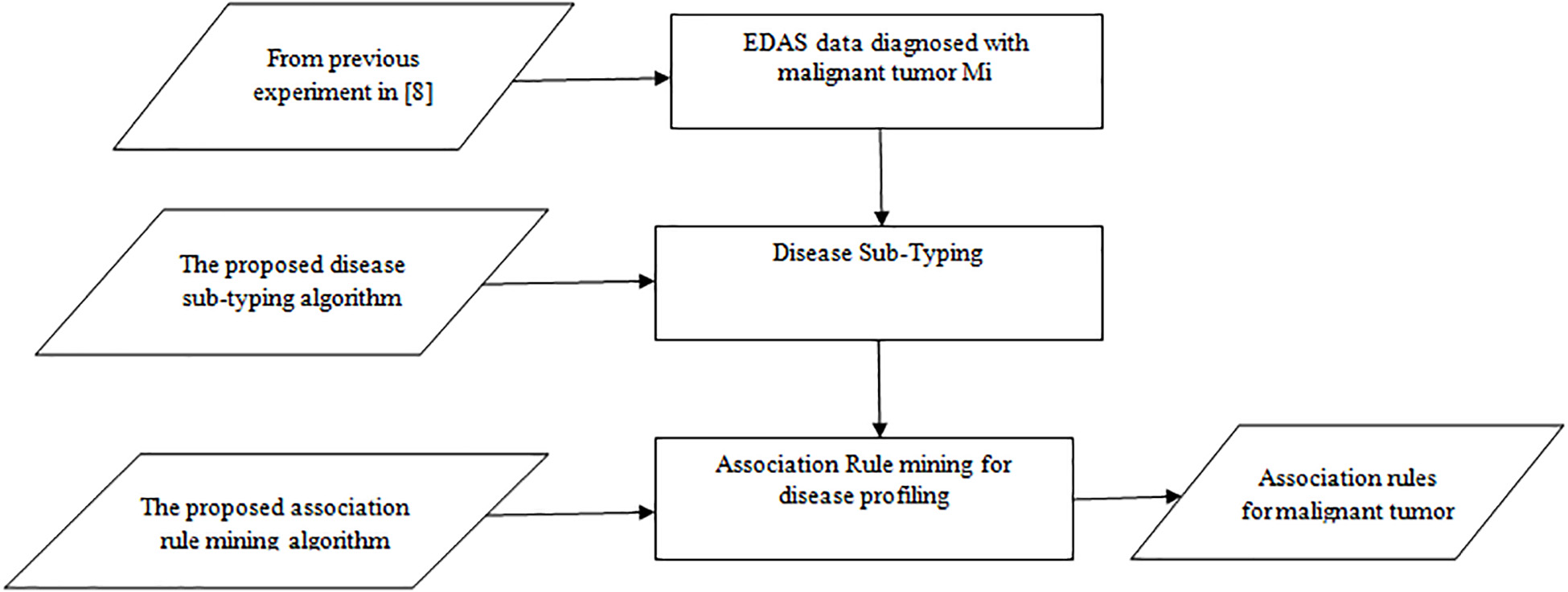
A Theoretical Approach for Correlating Proteins to Malignant Diseases
Malignant Tumors are developed over several years due to unknown biological factors. These biological factors induce changes in the body and consequently, they lead to Malignant Tumors. Some habits and behaviors initiate these biological factors. In effect, the immune system cannot recognize a Malignant Tumor as foreign tissue. In order to discover a fascinating pattern of these habits, behaviors, and diseases and to make effective decisions, different machine learning techniques should be used. This research attempts to find the association between normal proteins (environmental factors) and
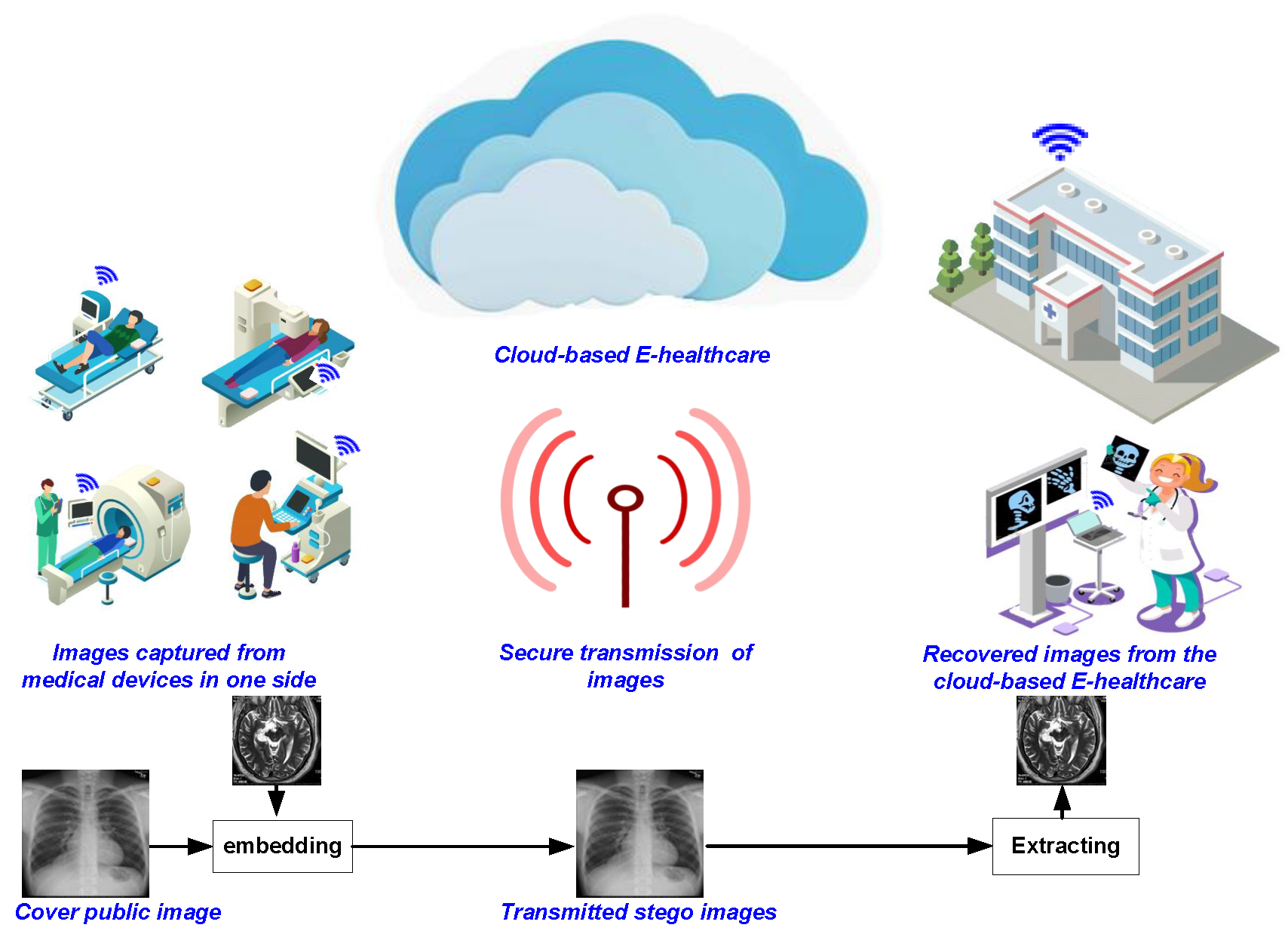
A robust quasi-quantum walks-based steganography protocol for secure transmission of images on cloud-based E-healthcare platforms
Traditionally, tamper-proof steganography involves using efficient protocols to encrypt the stego cover image and/or hidden message prior to embedding it into the carrier object. However, as the inevitable transition to the quantum computing paradigm beckons, its immense computing power will be exploited to violate even the best non-quantum, i.e., classical, stego protocol. On its part, quantum walks can be tailored to utilise their astounding ‘quantumness’ to propagate nonlinear chaotic behaviours as well as its sufficient sensitivity to alterations in primary key parameters both important
Tavaxy: Integrating Taverna and Galaxy workflows with cloud computing support
Background: Over the past decade the workflow system paradigm has evolved as an efficient and user-friendly approach for developing complex bioinformatics applications. Two popular workflow systems that have gained acceptance by the bioinformatics community are Taverna and Galaxy. Each system has a large user-base and supports an ever-growing repository of application workflows. However, workflows developed for one system cannot be imported and executed easily on the other. The lack of interoperability is due to differences in the models of computation, workflow languages, and architectures of
Combating sybil attacks in vehicular ad hoc networks
Vehicular Ad Hoc Networks (VANETs) are considered as a promising approach for facilitating road safety, traffic management, and infotainment dissemination for drivers and passengers. However, they are subject to an attack that has a severe impact on their security. This attack is called the Sybil attack, and it is considered as one of the most serious attacks to VANETs, and a threat to lives of drivers and passengers. In this paper, we propose a detection scheme for the Sybil attack. The idea is based on public key cryptography and aims to ensure privacy preservation, confidentiality, and non
Complexwavelet Transform Cwt Based Video Magnification for 3d Facial Video Identification
Magnifying micro changes in motion and brightness of videos that are unnoticeable by the human visual system have recently been an interesting area to explore. In this paper, we explore this technique in 3D facial video identification, we utilize this technique to identify 3D objects from 2D images. We present a Complex Wavelet Transform CWT, 2D-Dual CWT based technique, to calculate any changes between subsequent video frames of CWT sub-bands at different spatial locations. In this technique, a gradient based method is proposed to determine the orientation of each CWT sub band in addition to
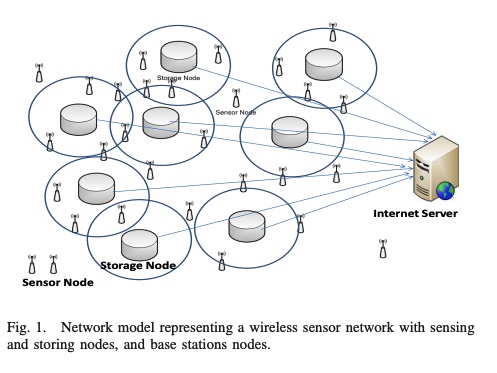
A distributed data collection algorithm for wireless sensor networks with persistent storage nodes
A distributed data collection algorithm to accurately store and forward information obtained by wireless sensor networks is proposed. The proposed algorithm does not depend on the sensor network topology, routing tables, or geographic locations of sensor nodes, but rather makes use of uniformly distributed storage nodes. Analytical and simulation results for this algorithm show that, with high probability, the data disseminated by the sensor nodes can be precisely collected by querying any small set of storage nodes.
Real-time scale-adaptive compressive tracking using two classification stages
In this paper, we describe a method for Scale-Adaptive visual tracking using compressive sensing. Instead of using scale-invariant-features to estimate the object size every few frames, we use the compressed features at different scale then perform a second stage of classification to detect the best-fit scale. We describe the proposed mechanism of how we implement the Bayesian Classifier used in the algorithm and how to tune the classifier to address the scaling problem and the method of selecting the positive training samples and negative training samples of different scales. The obtained
Change analysis for gait impairment quantification in smart environments
Visual Sensor Networks (VSNs) open up a new realm of smart autonomous applications based on enhanced three- dimensional sensing and collaborative reasoning. An emerging VSN application domain is pervasive healthcare delivery where gait information computed from distributed vision nodes is used for observing the wellbeing of the elderly, quantifying post-operative patient recovery and monitoring the progression of neurodegenerative diseases such as Parkinson's. The development of patient-specific gait analysis models, however, is challenging since it is unfeasible to obtain normal and impaired
Computer-aided analysis of fluorescein angiograms using colour leakage maps
Fundus fluorescein angiography (FFA) is a standard screening and diagnosis technique for several retinal diseases. The analysis of FFA images is performed qualitatively by skilled observers, and thus is vulnerable to inter- and intra-observer variability. In this study, the authors present a method for computer-aided analysis of FFA images. The method is based on generating quantitative colour fluorescein leakage maps (FLM) that mimic the thickness maps generated by the optical coherence tomography (OCT). Results from 64 patients show strong correlation between the FLM and OCT thickness maps
Pagination
- Previous page ‹‹
- Page 25
- Next page ››
