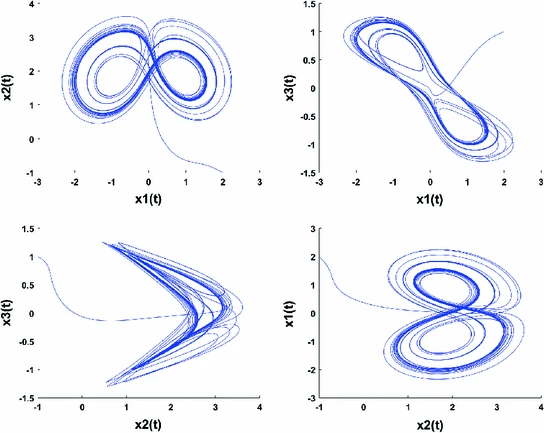
A study on coexistence of different types of synchronization between different dimensional fractional chaotic systems
In this study, robust approaches are proposed to investigate the problem of the coexistence of various types of synchronization between different dimensional fractional chaotic systems. Based on stability theory of linear fractional order systems, the co-existence of full state hybrid function projective synchronization (FSHFPS), inverse generalized synchronization (IGS), inverse full state hybrid projective synchronization (IFSHPS) and generalized synchronization (GS) is demonstrated. Using integer-order Lyapunov stability theory and fractional Lyapunov method, the co-existence of FSHFPS
Develop TE/TM Pass Filters on double-loaded-on-ridge Structure with ITO/TiN for Upstream FTTH Optical Access Networks
In this paper, TE/TM pass filters are introduced as a dual optical multiplexer in the fiber-to-the home (FTTH) uplink transmission. The architecture is implemented at 1330 nm wavelength, with a double-loaded-on-ridge structure. In the TE pass filter, TM mode couples with plasmonic mode while TE mode is guided through the core with low losses due to the effect of the two plasmonic materials. The TM mode is directed through the heart, though, in the TM pass filter. Transparent conductive oxides (TCOs) as Indium Tin Oxide (ITO), in addition to Titanium Nitride (TiN) are proposed as plasmonic
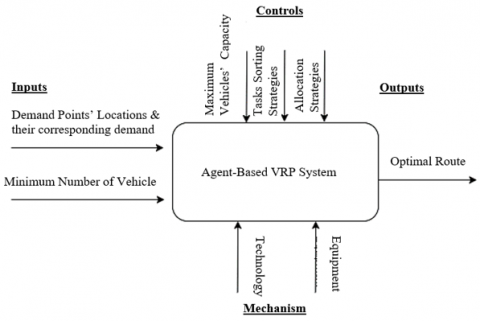
Modelling of agent-based vehicle routing problem using unified modelling language
The Vehicle Routing Problem (VRP) is among the most studied optimization problems in the field of supply chain management. Typically, VRP requires dispatching a fleet of vehicles from a central depot to deliver demand to pre-determined spatially dispersed customers, with the objective of minimizing the total routing cost, and the constraint of not exceeding vehicles' capacities. Agent Based Modelling (ABM) assists industries in the use of technology to support their decision-making process. This paper proposes a model of an Agent Based Vehicle Routing Problem System. The system under study is
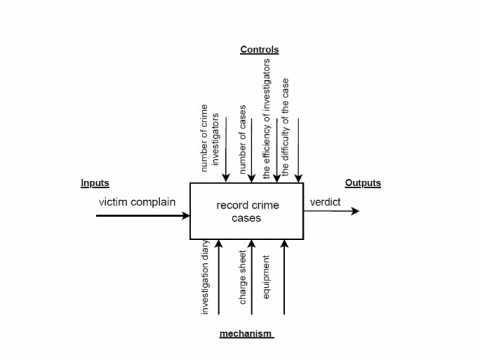
Modelling of Crime Record Management System Using Unified Modeling Language
Crime records management is a system that helps police keep records of citizens’ complaints files, investigation evidence and processes. In addition, it helps police keep records of the criminals who have been arrested or who are to be arrested. This paper aims to model the Crime Record Management System (CRMS) using various Unified Modeling Language (UML) diagrams, to demonstrate an explicit visualization of the system. Also, showing the communication among different actors, and the sequence of activities and interactions. The perspective of modeling the CRMS is by covering four stages, which
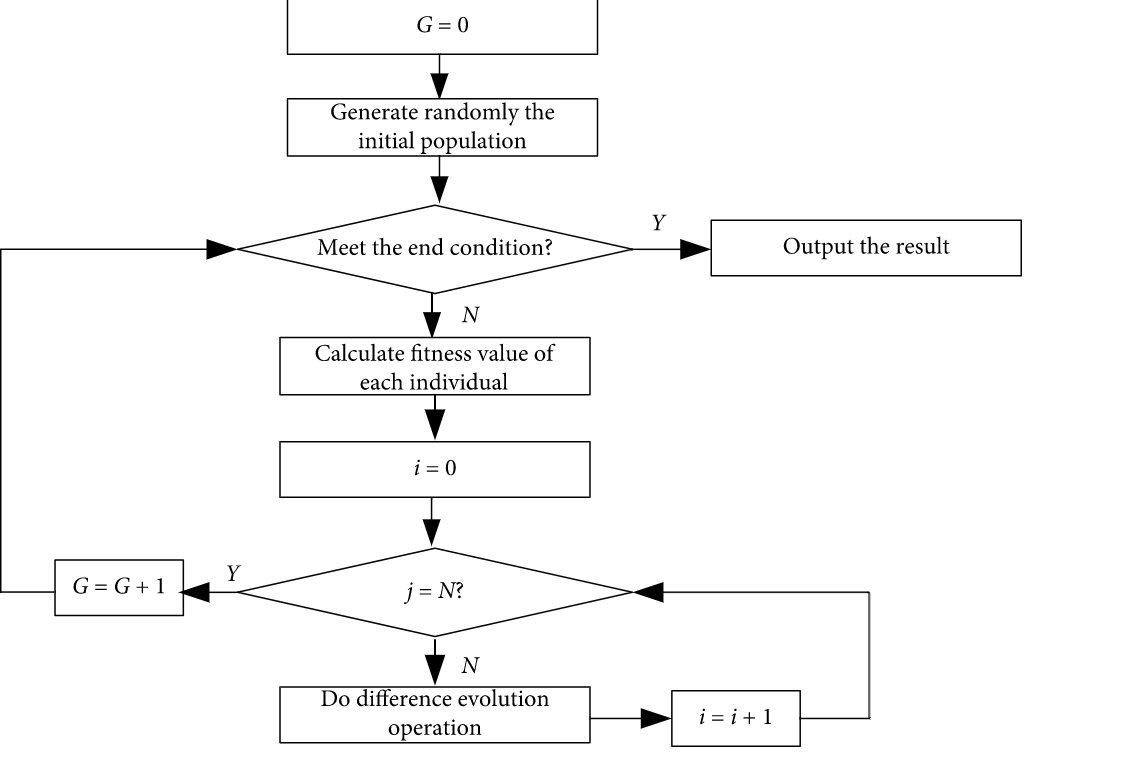
Enhanced Success History Adaptive de for Parameter Optimization of Photovoltaic Models
In the past few decades, a lot of optimization methods have been applied in estimating the parameter of photovoltaic (PV) models and obtained better results, but these methods still have some deficiencies, such as higher time complexity and poor stability. To tackle these problems, an enhanced success history adaptive DE with greedy mutation strategy (EBLSHADE) is employed to optimize parameters of PV models to propose a parameter optimization method in this paper. In the EBLSHADE, the linear population size reduction strategy is used to gradually reduce population to improve the search

Single-Objective Real-Parameter Optimization: Enhanced LSHADE-SPACMA Algorithm
Real parameter optimization is one of the active research fields during the last decade. The performance of LSHADE-SPACMA was competitive in IEEE CEC’2017 competition on Single Objective Bound Constrained Real-Parameter Single Objective Optimization. Besides, it was ranked fourth among twelve papers were presented on and compared to this new benchmark problems. In this work, an improved version named ELSHADE-SPACMA is introduced. In LSHADE-SPACMA, p value that controls the greediness of the mutation strategy is constant. While in ELSHADE-SPACMA, p value is dynamic. Larger value of p will
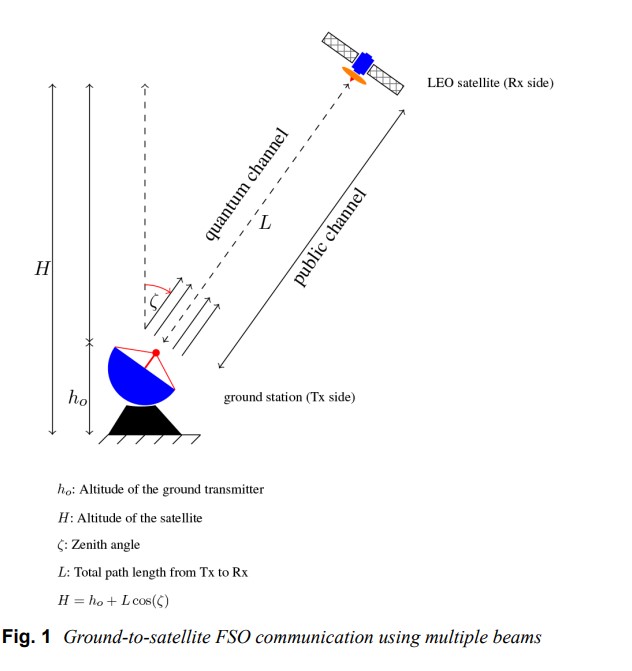
Performance evaluation and security analysis of ground-to-satellite FSO system with CVQKD protocol
This study evaluates the performance of a secure ground-to-satellite free-space optical (FSO) system using a bipolar pulse amplitude modulation over modulated gamma fading channel. A closed-form expression is derived for the joint probability of a satellite-based continuous-variable quantum key distribution (CV-QKD) protocol that uses dual-threshold detection. Furthermore, to study the system behaviour, closed-form expressions for quantum bit-error-rate (QBER) and quantum bitdiscard rate (QBDR) are given. The accuracy of the proposed derivations is validated using Monte-Carlo simulations and
Proactive Caching for Vehicular Ad hoc Networks Using the City Model
Caching at Roadside Units (RSUs) is a promising technique to alleviate the load on network backhaul in Vehicular AdHoc Networks (VANETs). It also allows us to minimize communications latency between RSUs and connected vehicles, which are interested in massive multimedia contents. This work proposes novel proactive caching schemes at RSUs for the city mobility environment. We adopt the Manhattan city model, where streets are arranged in an organized manner and movable nodes are allowed to traverse along the grid of horizontal and vertical streets. Exploiting the information about vehicles
Decentralized coded caching in wireless networks: Trade-off between storage and latency
This paper studies the decentralized coded caching for a Fog Radio Access Network (F-RAN), whereby two edge-nodes (ENs) connected to a cloud server via fronthaul links with limited capacity are serving the requests of K r users. We consider all ENs and users are equipped with caches. A decentralized content placement is proposed to independently store contents at each network node during the off-peak hours. After that, we design a coded delivery scheme in order to deliver the user demands during the peak-hours under the objective of minimizing the normalized delivery time (NDT), which refers
Proactive cognitive networks with predictable demand
In this paper we characterize the proactive diversity gain of a cognitive network with predictable primary and secondary requests. Network performance is analyzed under two proposed proactive service policies that preserve higher priority for the primary user. The first policy preserves the primary diversity bound as if there is no secondary user in the network, whereas the second policy boosts the secondary diversity with guaranteed higher primary diversity. For each policy, we derive diversity gain bounds for primary and secondary users. We show that the predictability of secondary requests
Pagination
- Previous page ‹‹
- Page 17
- Next page ››
